Operational Technology Cybersecurity Market Growth Drivers, Key Players, Trends and Regional Insights by 2034
Operational Technology (OT) Cybersecurity Market Size & Trajectory
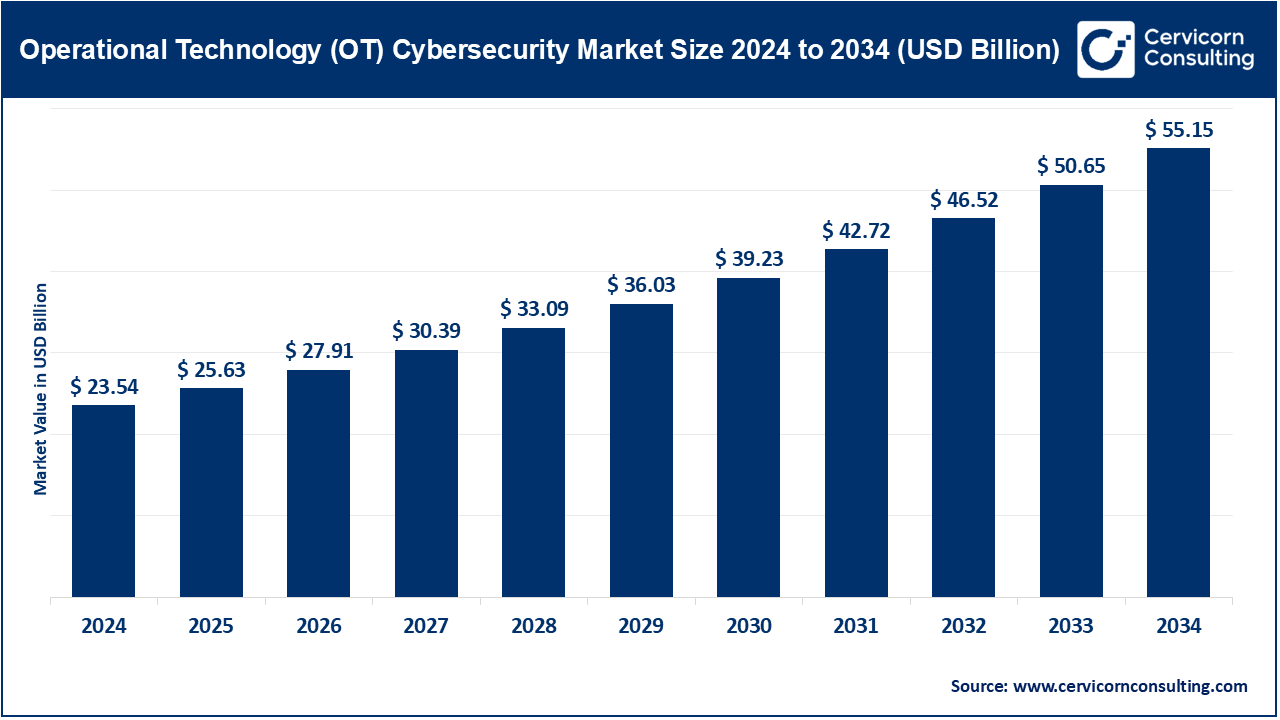
The global operational technology (OT) cybersecurity market is projected to grow significantly over the coming years. Research indicates that the market is expected to expand from around USD 23.54 billion in 2024 to USD 55.15 billion by 2034, reflecting a strong CAGR of 16.4%.
Other forecasts also predict double-digit growth driven by increasing adoption of IIoT, regulatory mandates, and the rising sophistication of cyberattacks targeting industrial infrastructure. These projections reflect broad demand across energy, manufacturing, utilities, transportation, and other critical infrastructure sectors.
What is the Operational Technology (OT) Cybersecurity Market?
Operational Technology (OT) cybersecurity is the market that supplies tools, services, and programs designed to protect industrial control systems (ICS), SCADA, distributed control systems (DCS), programmable logic controllers (PLCs), industrial IoT (IIoT) devices, and other physical-process-control systems from cyber threats. The OT cybersecurity market includes products for asset discovery and inventory, protocol-aware threat detection and prevention, network segmentation and boundary protection, secure remote access, anomaly detection using behavioral and machine learning techniques, incident response, and managed security services tailored to operational environments. OT cybersecurity is distinct from pure IT security because it must preserve availability and safety of physical processes while often working with legacy, protocol-constrained devices.
Operational Technology (OT) Cybersecurity Market — Growth Factors
The OT cybersecurity market is accelerating due to a confluence of factors: rapid IIoT adoption that expands the OT attack surface; increased IT–OT convergence that exposes industrial networks to enterprise threats; a rise in disruptive, high-impact attacks on critical infrastructure sectors such as energy, water, transportation, and manufacturing that force organizations to prioritize uptime-safe security controls; regulatory pressure and industry standards mandating stronger protections and reporting; broader use of cloud and remote access for industrial operations creating new risk vectors; and growing adoption of AI/ML in threat detection and response which both empowers defenders and changes attacker tactics. Together, these forces are driving heightened budgets for specialized OT visibility, segmentation, and incident response solutions, pushing the market to double (and in many projections, more than double) over the next 5–7 years.
Get a Free Sample: https://www.cervicornconsulting.com/sample/2719
Why OT Cybersecurity is Important
OT systems control the physical world — power generation and distribution, water treatment, manufacturing lines, transportation signals, oil & gas pipelines, and building systems. A cyber incident in OT can cause physical damage, environmental harm, safety risks, extended downtime, and cascading economic effects. Unlike many IT breaches where data confidentiality is the central concern, OT attacks frequently threaten availability and safety, making OT cybersecurity critical not only for business continuity but for public safety and national security. OT environments also contain long-lived, legacy devices that were never built for connectivity or security, so specialized tools and processes are required to detect anomalies without disrupting operations.
Operational Technology (OT) Cybersecurity Market — Top Companies
Cisco Systems, Inc.
- Specialization: Networking and infrastructure-first security; converged IT/OT visibility and enforcement.
- Key focus areas: OT/ICS visibility (Cisco Cyber Vision), industrial threat defense, network-as-a-sensor approach, segmentation, secure remote access for industrial environments, integration between Cisco Secure products and industrial switches/routers.
- Notable features: Deep integration of OT visibility into network hardware, adaptive segmentation, zero-trust remote access tailored for ICS, and a broad portfolio bridging IT and OT.
- 2024 revenue (companywide): Approximately USD 53.8 billion.
- Market share / presence: Cisco is a major global infrastructure and security player, widely present across enterprises and critical infrastructure operators worldwide.
Palo Alto Networks, Inc.
- Specialization: Next-generation firewalls, integrated security platform, threat intelligence, and MDR services; expanding OT coverage via integrations and threat intel.
- Key focus areas: Platform consolidation (Cortex, Prisma), threat intelligence from Unit 42, XDR and network segmentation, secure remote access, and zero-trust architectures that extend to OT environments.
- Notable features: Strong threat intelligence (Unit 42), integrated XDR approach, and extensive incident response capabilities.
- 2024 revenue (fiscal year 2024): Approximately USD 8.0 billion.
- Market share / presence: A leading global cybersecurity platform provider with expanding OT security offerings.
Fortinet, Inc.
- Specialization: Security fabric with OT-aware functions — deep visibility, segmentation, secure connectivity, and centralized management for OT use cases.
- Key focus areas: OT-aware Fortinet Security Fabric, FortiGuard OT threat intelligence, and ruggedized products for industrial environments.
- Notable features: Integrated approach covering edge-to-cloud, strong firewall and segmentation capabilities, and OT-focused services across the Purdue model.
- 2024 revenue (companywide): Approximately USD 6.0 billion.
- Market share / presence: Frequently ranked as a leader in network and OT protection, with a strong global presence in industrial verticals.
Check Point Software Technologies Ltd.
- Specialization: Advanced threat prevention, protocol-aware firewall, and ICS/OT protections; ruggedized gateway appliances for industrial environments.
- Key focus areas: ICS/OT threat prevention, quantum-rugged/industrial gateways, IT/OT segmentation, and integration with managed detection services.
- Notable features: Quantum Rugged security gateways, support for SCADA protocols, and emphasis on passive monitoring that transitions to active prevention without disrupting operations.
- 2024 revenue (companywide): Approximately USD 2.56 billion.
- Market share / presence: Well-established cybersecurity vendor with a global footprint in enterprise and industrial sectors.
IBM Corporation
- Specialization: Consulting-led OT security services, threat intelligence, incident response, and managed detection & response for industrial environments.
- Key focus areas: Risk assessments, monitoring, incident response, integration of threat intelligence, compliance support, and OT transformation.
- Notable features: Strong professional services footprint, integration of SOC with OT monitoring, and extensive global consulting reach.
- 2024 revenue (companywide): Approximately USD 62.8 billion.
- Market share / presence: A global leader in consulting and managed security, frequently chosen by utilities, governments, and large industrial enterprises for complex OT cybersecurity programs.
Leading Trends and Their Impact
- IT–OT convergence and remote operations: Unifying IT and OT environments increases the attack surface, driving demand for solutions that operate safely within control systems.
- IIoT proliferation: The exponential growth of connected devices requires stronger asset discovery and monitoring capabilities.
- Rise of infrastructure-targeted adversaries: Nation-state and ransomware actors increasingly disrupt industrial operations, pushing demand for managed detection and response services.
- Protocol-aware detection and behavioral analytics: OT-specific protocols necessitate specialized tools that establish baselines and detect anomalies.
- Regulatory and compliance pressure: Governments and regulators mandate higher standards for cybersecurity in critical infrastructure.
- AI and ML integration: Enhanced anomaly detection capabilities are improving defenses, though adversaries also exploit these technologies.
Successful Examples of OT Cybersecurity Deployments Worldwide
- Utilities in Europe: Implemented segmentation and monitoring solutions to separate corporate IT from grid control systems, improving resilience and reducing lateral movement risks.
- Manufacturing in North America: Adopted passive visibility tools with managed detection and response services, minimizing downtime and avoiding production disruptions.
- Oil & Gas in the Middle East: Deployed zero-trust remote access for field engineers, improving remote work security across distributed sites.
- Critical Infrastructure in the UK: Strengthened OT monitoring and leveraged government threat intelligence programs to secure building systems and industrial operations.
Global Regional Analysis — Adoption, Government Initiatives, and Policies
North America
- High adoption across energy, manufacturing, utilities, and transportation sectors.
- Strong government programs such as CISA guidelines, NIST frameworks, and incident reporting mandates drive adoption.
Europe
- Focus on critical infrastructure resilience through the EU NIS2 Directive and national-level cybersecurity regulations.
- Public-private partnerships emphasize information sharing and cross-sector resilience.
Asia-Pacific
- Rapid adoption due to growing IIoT deployments in manufacturing and utilities.
- Governments in China, India, Japan, South Korea, and Australia are implementing stricter cybersecurity standards for critical infrastructure.
Middle East & Africa
- Heavy investments in OT security in the oil & gas and energy sectors.
- National resilience strategies and cybersecurity frameworks are encouraging partnerships with global vendors.
Latin America
- Growing adoption in utilities and large industrial enterprises.
- Governments are advancing regulatory maturity and cross-border cooperation on critical infrastructure security.
Policy & Procurement Trends Affecting Vendors and Buyers
- Mandatory incident reporting and compliance standards are pushing organizations to strengthen monitoring and detection.
- Integrated solutions and managed services are in demand due to limited in-house OT security expertise.
- Public-private partnerships and resilience funds are accelerating modernization and investment in OT cybersecurity infrastructure.
To Get Detailed Overview, Contact Us: https://www.cervicornconsulting.com/contact-us
Read Report: U.S. Long-Term Care Market Trends, Growth Drivers and Leading Companies 2024